SECURITY & FRAUD DETECTION
Secure, safe payments.
- Fraud detection with responsive warnings.
- Notification of changes to vendor bank account details.
- No more compromised cards to shut down and replace.
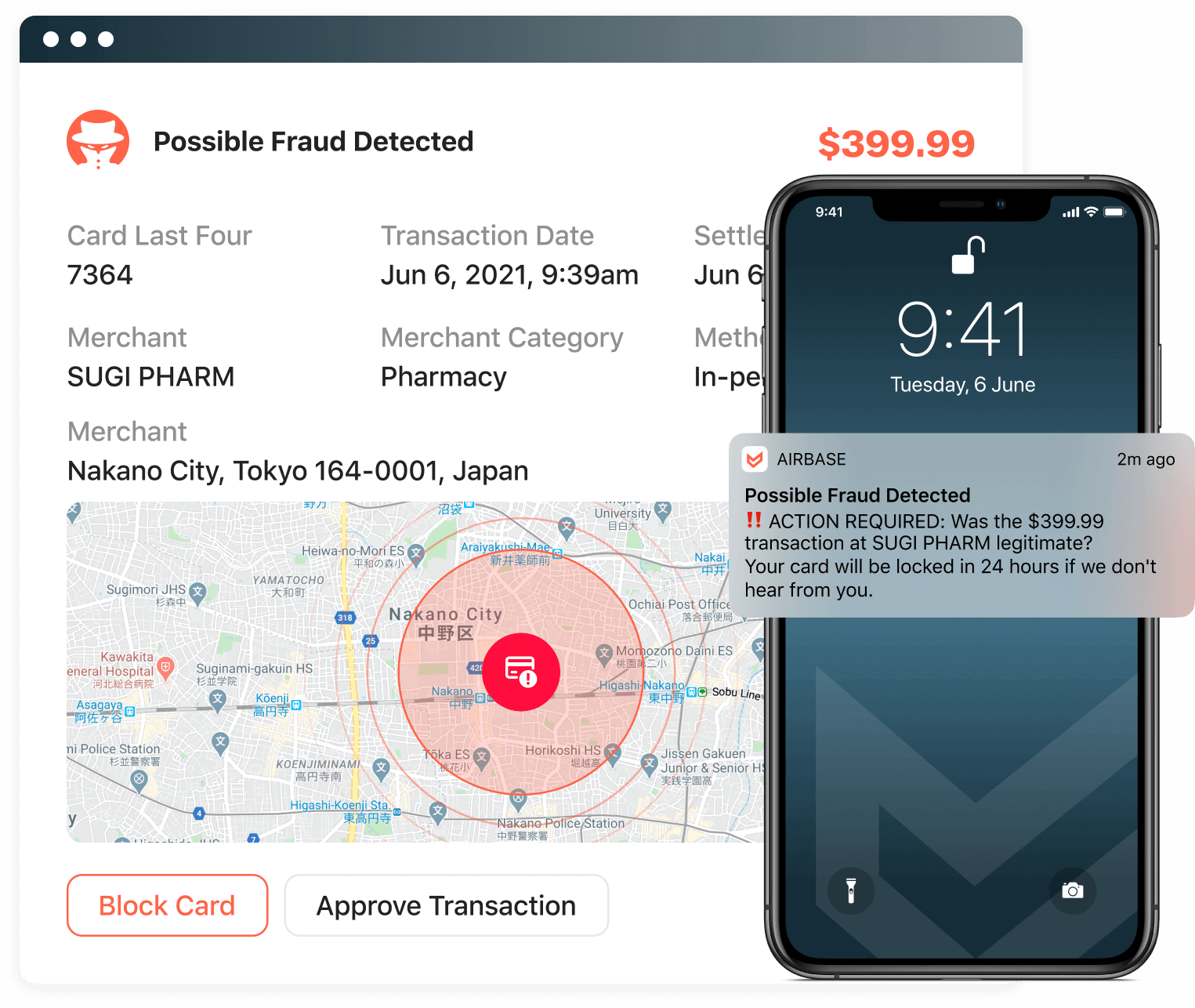
Add a layer of protection from scammers.
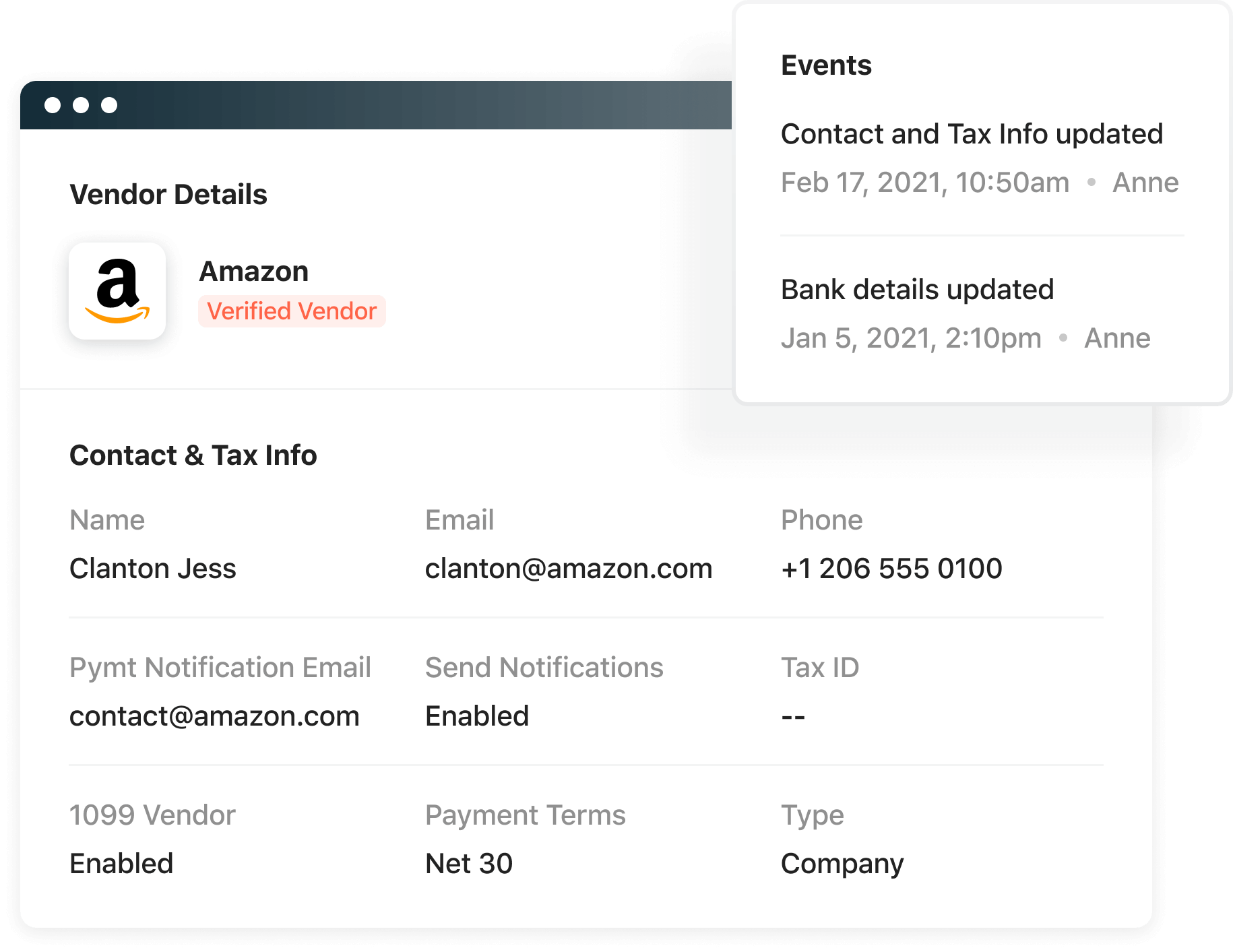
A prime target for fraud is by falsifying bank account details. In Airbase, any changes to a vendor bank account require approval to protect AP teams from falling victim. Two-factor authentication for bank account changes via the vendor portal helps protect vendors from scams.
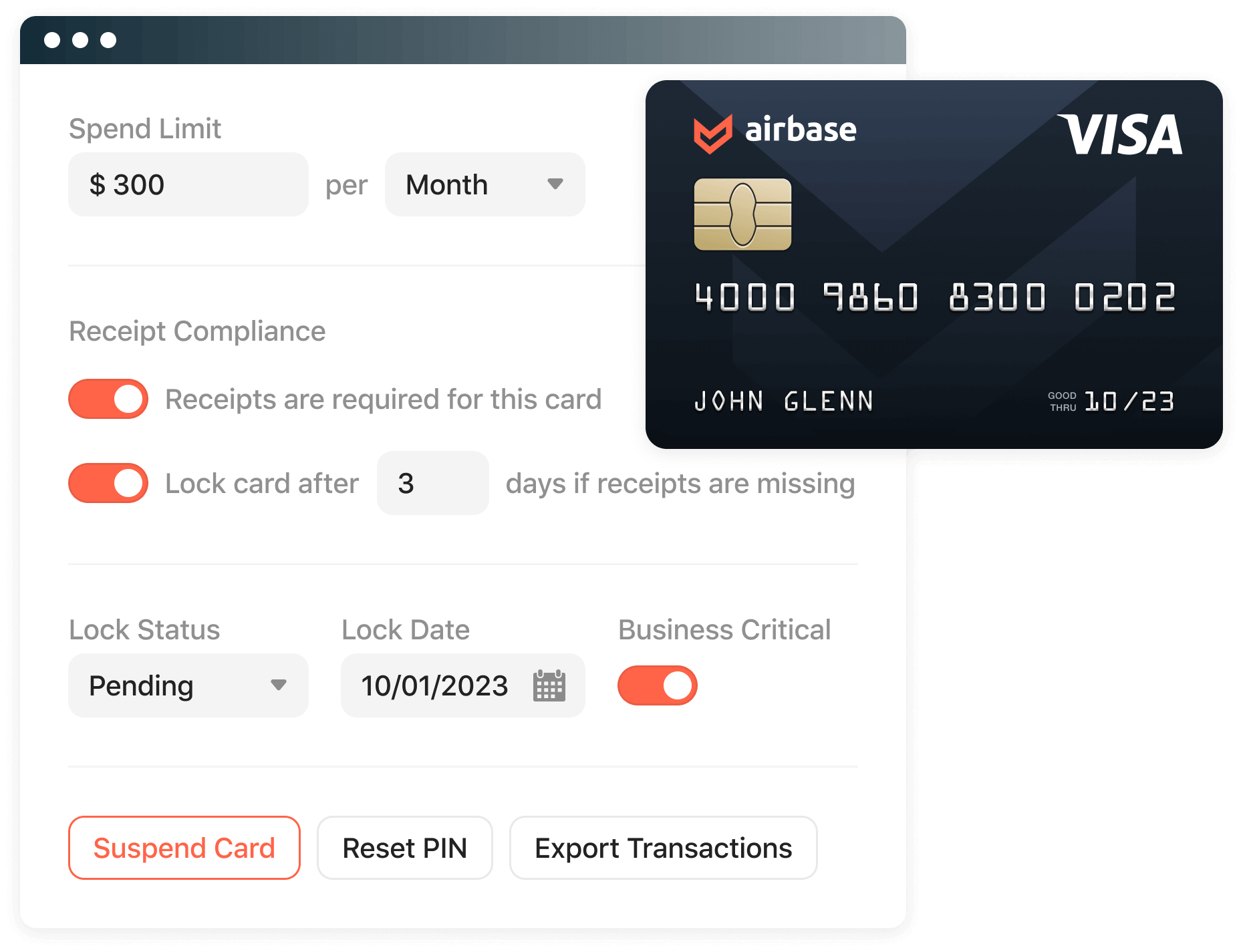
Set controls and limits. Lock and unlock a card.
When cards have spend limit and expiration restrictions on them, the amount at risk to fraud is limited. Because virtual cards are generated as needed by the person making the purchase, there are no opportunities for vendor fraud associated with their use.
A card that is lost or stolen can be easily locked and then unlocked, if found, from your dashboard.
Fraud detection & notification.
Card owners are immediately notified if a suspected fraudulent charge has been attempted. These alerts are sent to your email, and also appear on your dashboard. If the cardholder verifies the charge as legitimate, it will go through. Airbase adjusts its algorithm to include approved vendors to ensure future transactions are processed.
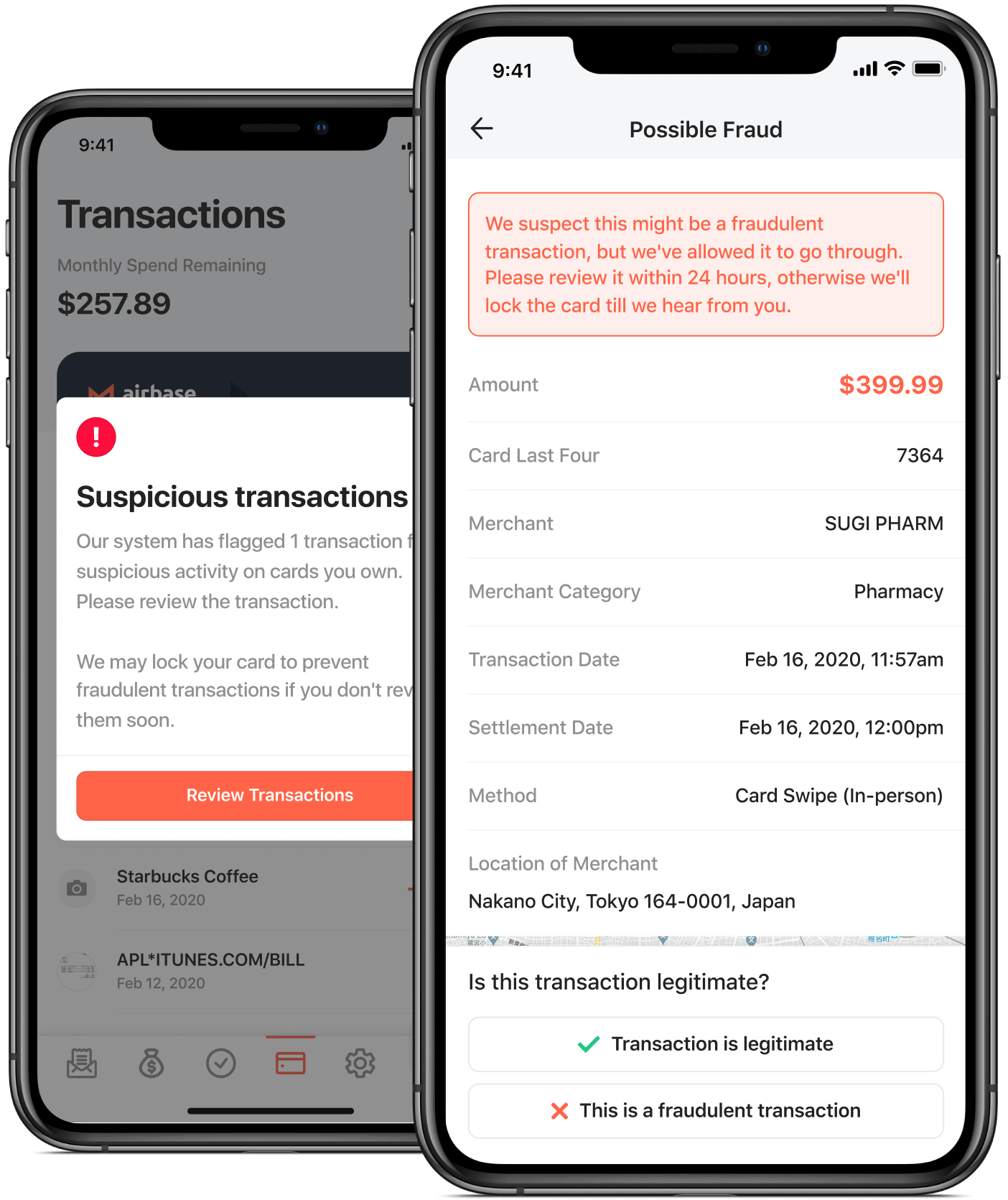

Never waste time on a compromised card again.
If a corporate card does get compromised, it’s the finance team who are asked to track down all recurring expenditures on the card, and replace it with a new one. The Airbase system allows you to make vendor-specific virtual cards so that this problem won’t arise.
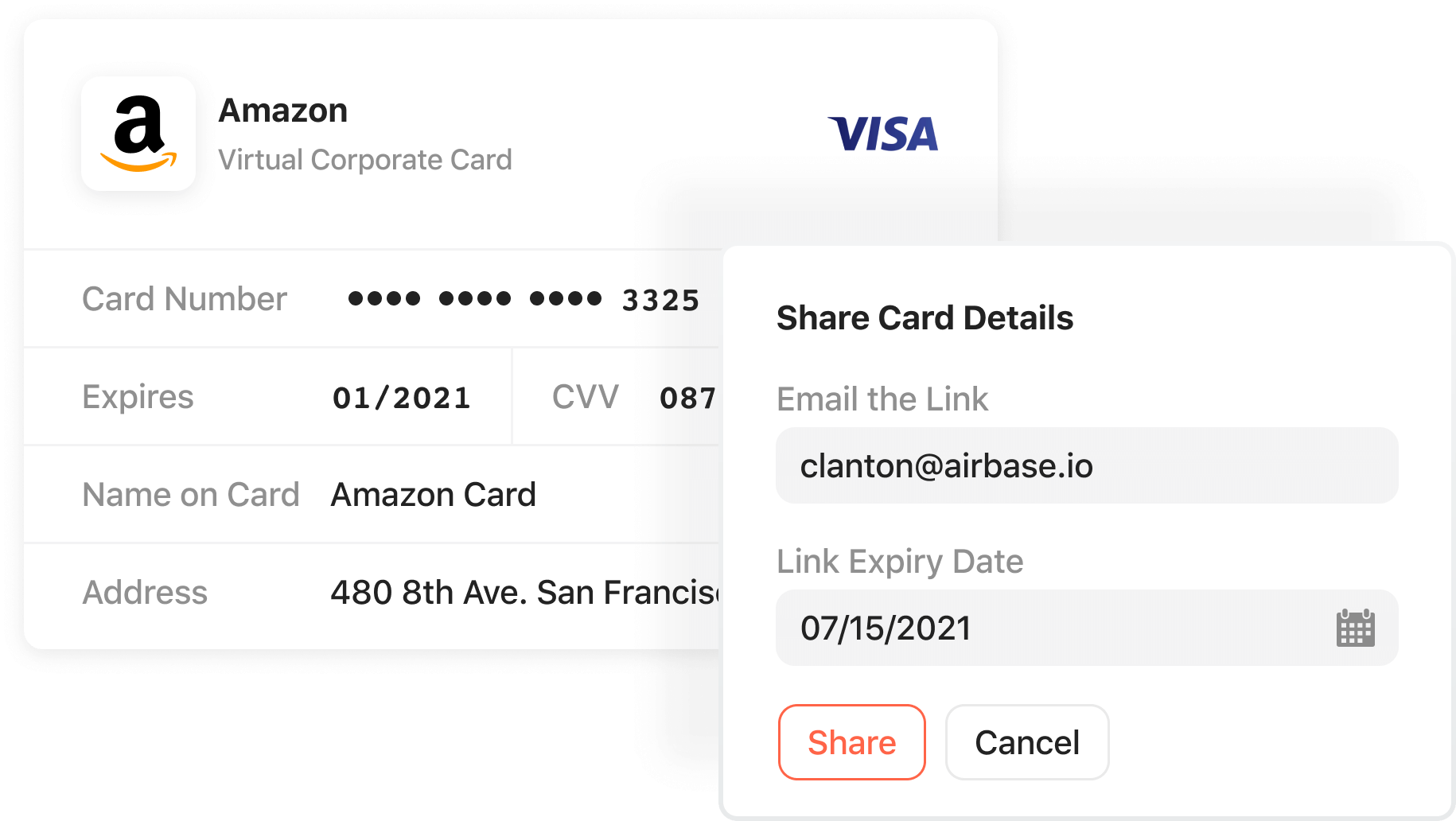
Safely share card details with colleagues.
Sharing virtual card details in an email, or online chat, can compromise the security of the card.
We created a “Share” feature so that card details can be securely shared with other members in the organization and, in some cases, with external contractors.
For example, a purchase manager can share the card details with an assistant for an authorized spend.
Protecting vendor accounts.
When vendors manage their account details through our Vendor Portal, you don’t need to worry about whether an email requesting an update of account details is valid or not.

Airbase is a SOC 2 Type II and
SOC 1 Type II compliant company.


“The fraud protection that Airbase offers is another great value add. If anyone changes the vendor, or if vendor bank details change, we get a notification to review and approve those changes. That additional layer of control for a controller ensures we’re paying the right bills to the right third parties.”
Eoin Hession
Controller at Medely

 Jira
Jira  Ironclad
Ironclad  Asana
Asana 


